Figuring out any computational system’s Achilles’ heel won’t be a trouble-free job as it might be before. Hackers are you listening! Period.
Algorithms now are so progressive that deducing future trends is just a matter of few lines of codes. For instance, alogs can calculate which post might pull the maximum readership, on what topic one gets the highest number of tweets or how many times one scans own pic after uploading on facebook (this one’s for datasexuals).
Coders of these softwares would hate hackers doing reverse engineering in their programs and tweaking around the source code. After all, no one likes people fiddling around with their trade secrets. In order to remove this intimidation from hackers, computer scientists from the University of California, Los Angeles, IBM Research, and the University of Texas at Austin are developing a scheme called the mathematical obfuscation.
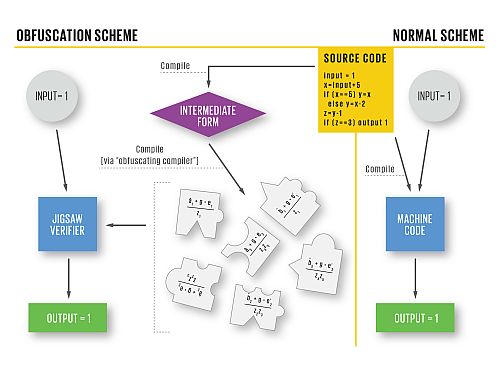
Converting the underlying code into math puzzles that’d take years to resolve, the scientists aim to protect the softwares’ vulnerability.
Normally, a program works in three stages:
1) Programs are written in code languages, which are easily comprehended by humans. Php, python, C++, .Net, Ruby are some of the well-known programming languages.
2) Compiler, another computer program interprets the human written script into machine code. Or it gives a set of instructions that can be executed by the CPU.
3) At the final stage, output is processed as the input statements given, which we see on the screen.
Introduction of mathematical obfuscation at the compiler stage:
Once the program reaches the compiler level, the code is transformed into an intermediate form for an obfuscating compiler, which further converts the form into mathematical jigsaw puzzle.
A new program that is written in machine code is introduced at this stage. It’s job would be to verify the jigsaw by taking the puzzle pieces along with all the inputs with the aim of assembling them. Once the system teaser is complete with the arrangement of correct pieces, it will then instruct the CPU to produce accurate output.
Cases where hackers try to fiddle around with the source code, the pieces won’t fit and hence the consequential output would be useless. The ‘modified software’ would fail to give the required insights. In fact, the workings would stand nowhere near to the original ones.
Obfuscation does require huge amount of computation for practical application and the team – Sahai, Sanjam Garg, Craig Gentry, Shai Halevi, and Mariana Raykova of IBM Research, and Brent Waters, an assistant professor of computer science at the University of Texas at Austin – is confident that they can make it a reality.
A Boon or Bane
Some anti-virus softwares might consider it as harmful intent tagging the code as malicious.
While on the other side, obfuscation truly would be a boon for softwares whose inner matrix is revealing enough for inviting vulnerabilities. Security patches is one such gateway through which the hackers enter and tug around the source code.
Credit: IEEE Spectrum